This is your introduction to Cyber Threat Intelligence, in this section, we will go over a few concepts that are crucial for you to understand before moving forward.
The topics of this section includes the following:
- Disclaimer
- What is cyber threat intelligence or CTI?
- What is Open-Source intelligence (OSINT)?
- Why CTI is important for national security?
- Examples of underground cyber crime sites
Disclaimer
This course is designed for educational purposes only. It aims to help students, researchers, security professionals, and threat intelligence analysts understand cyber-crime ecosystems and defensive techniques. The course includes demonstrations of tools, technologies, and methodologies used to study cyber threats, including public and underground sites, AI models, and web scraping frameworks.
By participating in this course:
- You agree not to use any information, tools, or techniques provided for unlawful purposes.
- You must follow all applicable local, national, and international laws when conducting any form of intelligence gathering, analysis, or related activity.
- The course creators and providers do not endorse or encourage access to, interaction with, or participation in any illegal marketplaces, services, or activities.
- Any references to criminal sites, actors, or activities are purely for educational analysis and awareness.
- Engaging with or attempting to access criminal infrastructure without proper legal authority could expose you to criminal liability.
It is your responsibility to ensure that your use of the knowledge and skills from this course complies with all legal and ethical standards in your jurisdiction. The course provider, instructors, and affiliates accept no responsibility for any misuse or illegal application of the materials presented.
If in doubt, consult with legal counsel or your organization’s compliance team before applying any techniques covered in this course outside of a controlled lab environment.
What is Cyber Threat Intelligence (CTI)?
Cyber Threat Intelligence (CTI) is the process of collecting and analyzing information about cyber threats so that an organization can defend itself. It is about turning raw data into useful knowledge that helps you:
- Understand who might attack you
- Know what methods they might use
- Take steps to prevent, detect, or respond to these threats
CTI is not just looking for threats. It is about gathering the right information, understanding it, and using it to make better security decisions.
Our goal in this course is to identify initial access brokers who discuss selling access to Canadian companies on cyber crime sites.
Identifying Initial Access Brokers (IABs)
Suppose a CTI team is trying to protect a company from ransomware attacks. One way ransomware gangs break into companies is by buying access from Initial Access Brokers (IABs). This access could include remote access into your company's network through RDP or a web shell. Depending on the access type and the privileges attackers have acquired, they might increase or decrease the value of the IAB access.
An IAB is a criminal who gains entry into a company's network using stolen passwords, malware, phishing, or by exploiting security vulnerabilities. Instead of launching an attack themselves, the IAB sells that access to other criminals. IABs can sometimes be insider threats or malicious employees.
Here’s where CTI comes in. A CTI team might:
- Monitor dark web forums and chat groups where IABs advertise access for sale
- Find a post that says something like: "Selling domain admin access to a manufacturing firm in Germany. $8,000."
- Collect details such as what kind of access is being sold, how recent the post is, and whether the description matches their company or one of their clients
- Analyze this information and report it to the right people so action can be taken
In this way, CTI helps detect that an IAB has compromised a company before a ransomware group buys that access and launches a damaging attack.
What is OSINT?
Open Source Intelligence (OSINT) is information collected from public sources that anyone can access. OSINT can come from:
- Websites
- News articles
- Social media
- Hacker forums
- Paste sites where data breaches are shared
- Public records
CTI teams use OSINT to find signs of threats. For example, they might search hacker forums (which are public or semi-public) to look for IABs selling access. OSINT is mainly passive information gathering.
What is passive information gathering?
Passive information gathering means collecting data without interacting with the target’s systems. The target does not know they are being investigated.
Examples:
- Reading hacker forum posts
- Searching for leaked credentials in public data dumps
- Looking up domain registration details
- Scanning news reports or social media for clues
Passive gathering is low risk because you are not touching the target’s systems or interacting with criminals.
Active information gathering for identifying IABs
When it comes to identifying IABs, active information gathering means directly interacting with sources or platforms where IABs operate to collect more detailed or hidden information. Unlike passive gathering, this could involve activity that the IAB or the platform notices.
Here are examples of what active information gathering might look like when trying to identify IABs:
- Creating accounts and engaging on underground forums where IABs sell access. For example, a CTI analyst may register on a dark web marketplace or hacker forum and ask questions or respond to IAB advertisements to gain more details about the seller or the access being offered.
- Direct messaging or interacting with suspected IABs in private channels or encrypted messaging apps to collect intelligence on what access they are offering and which companies are being targeted.
- Placing a controlled "purchase" or bait request to verify what the IAB is really selling or to gather attribution information (this is often done in coordination with law enforcement).
In these cases, active gathering involves interaction that goes beyond simply observing public posts. It is riskier because:
- The IAB may notice that they are being investigated
- It could lead to operational security risks for the CTI team
- Legal and ethical boundaries must be carefully managed
Why CTI is important for national security?
Cyber Threat Intelligence (CTI) plays a critical role in national security because cyber-crime is no longer just about stealing credit cards or spreading viruses. Today, cyber-criminals and nation-state actors target critical infrastructure, supply chains, government agencies, healthcare systems, and private companies. They aim to cause disruption, steal sensitive information, and weaken economies. Identifying these threats early helps protect not just individual organizations, but entire countries.
A realistic CTI example: spotting an IAB
Imagine a CTI analyst monitoring dark web forums notices this post:
“Selling domain admin RDP access to an energy company in Eastern Europe. Access is fresh, stable. $10,000. Only serious buyers.”
This is a clear case of an Initial Access Broker (IAB) offering to sell access to a critical infrastructure company. If a ransomware group or a hostile nation-state buys this access, they could:
- Shut down energy grids
- Steal sensitive engineering data
- Cause a regional blackout
The CTI analyst’s job here is to:
- Collect information about the post, such as the IAB’s username, the description of the company, the type of access, and how the access was obtained.
- Verify and analyze whether the company is known, if the access is real, and what the risk is.
- Report and act, either by alerting the company directly (if the target is identifiable) or working through law enforcement.
This work helps prevent cyberattacks that could harm not just the company, but an entire region or country.
How can you help?
While CTI operations on criminal forums often require expertise, individuals like you can contribute within the law using OSINT and passive information gathering techniques such as:
- Report data breaches or leaks: If you spot company credentials or sensitive data posted on public sites (for example, paste sites or social media), they can alert the company’s security team or national cyber agencies.
- Monitor public forums and social media: Analysts with cyber-security knowledge can legally follow open discussions and report suspicious activity.
- Share indicators of compromise (IoCs): If someone notices phishing domains, malicious IP addresses, or other technical signs of a possible attack, they can report them to public threat-sharing platforms or Canadian Centre for Cyber Security (CCCS).
It is important that individuals do not try to interact directly with cyber-criminals or enter restricted criminal marketplaces without proper authorization, as this could break the law or put them at risk.
The vast scale of the cybercrime landscape
The cybercrime world is enormous and complex:
- Many IABs and cybercriminals do not advertise on English-speaking forums. Instead, they operate on Russian-language forums, Chinese-language forums, and other non-English marketplaces that are hard to monitor without language skills and cultural understanding.
- Threat actors often use private channels, encrypted messaging apps, or invitation-only marketplaces that are not visible through normal internet searches.
- The volume of threats is so large that most cybercrime activity never reaches public attention. For every forum post selling access, there are many private deals, coordinated attacks, and hidden operations.
This means CTI is essential not just for companies but for national defense, because a single undetected IAB sale could lead to:
- Attacks on hospitals, transport networks, or water systems
- Espionage against government agencies
- Disruption of elections or economic harm
Examples of Underground Cybercrime Sites
To better understand the cybercrime ecosystem, it is helpful to examine what real cybercrime sites look like. Most cybercrime sites operate on the Tor network, though some can be found on the clearnet as well. These "sites" or "websites" are also commonly referred to as "forums."
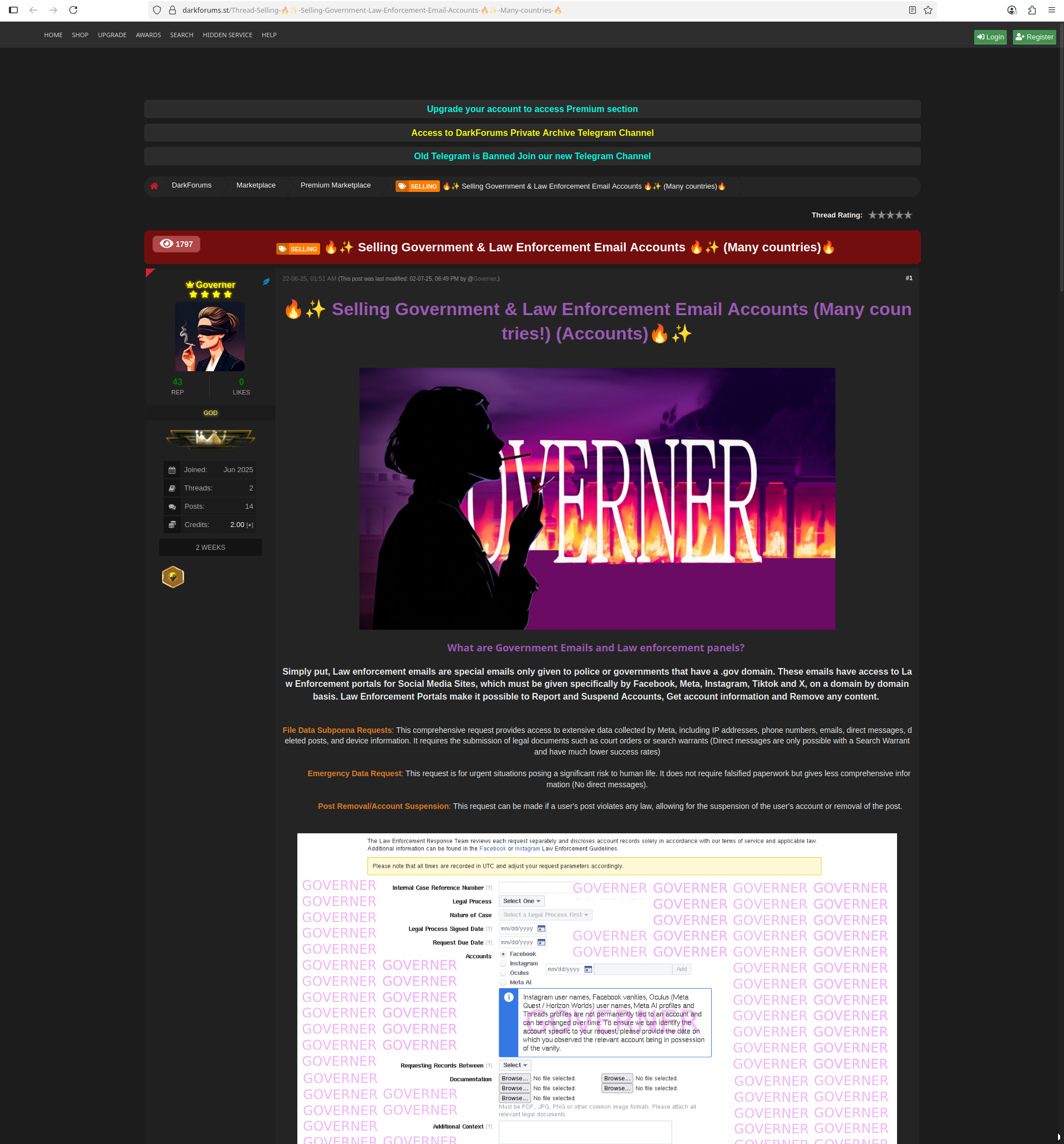
darkforums.st
darkforums.st is an example of a cybercrime forum that you can access through a regular browser as of July 6th, 2025.
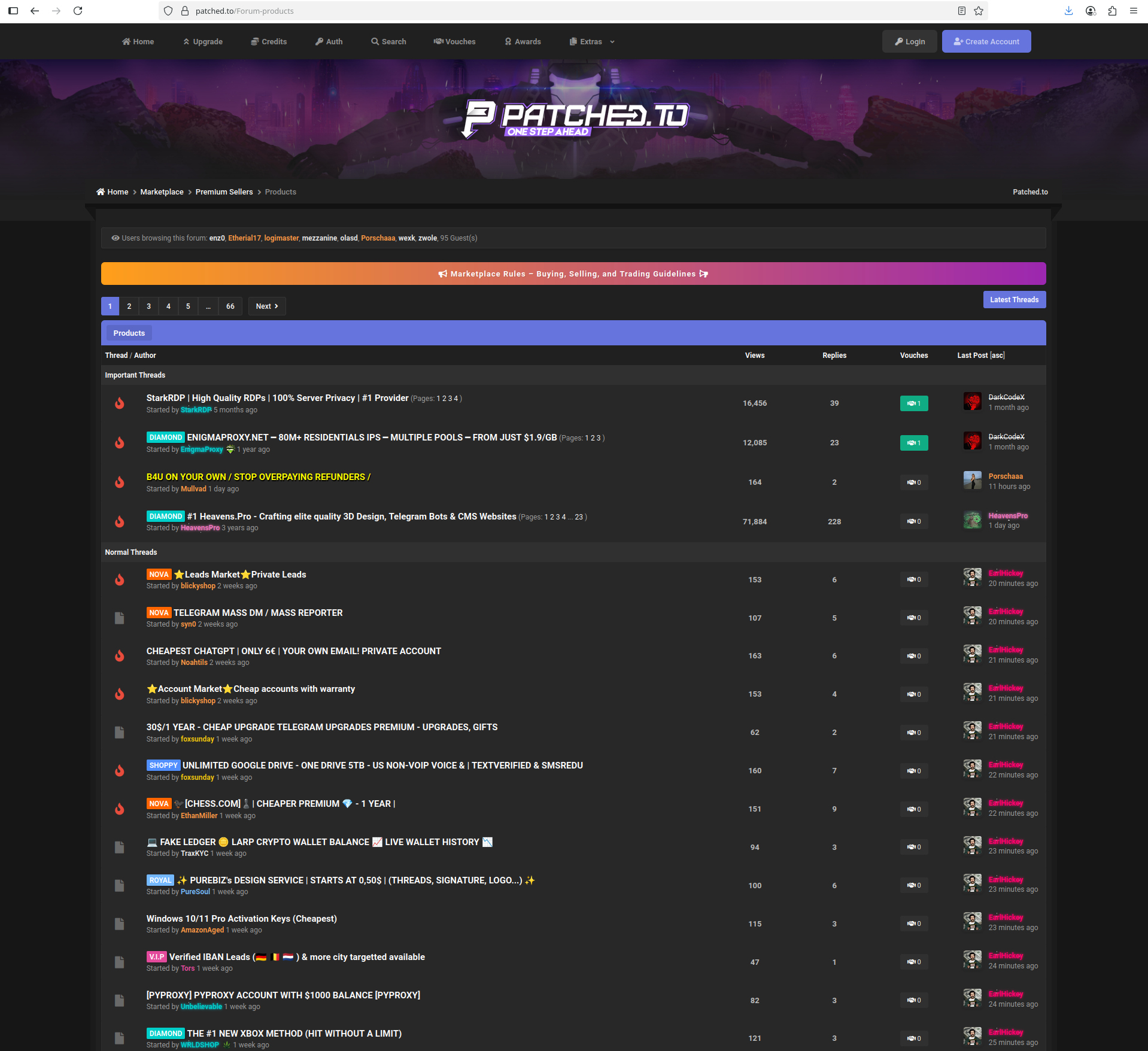
patched.to
There is also patched.to where people sell cracked software and stolen accounts:
altenens.is
Some forums are specifically designed to scam as many people as possible, not everything you see on hacking forums is legitimate. For example, on altenens.is, there are people selling carding methods:
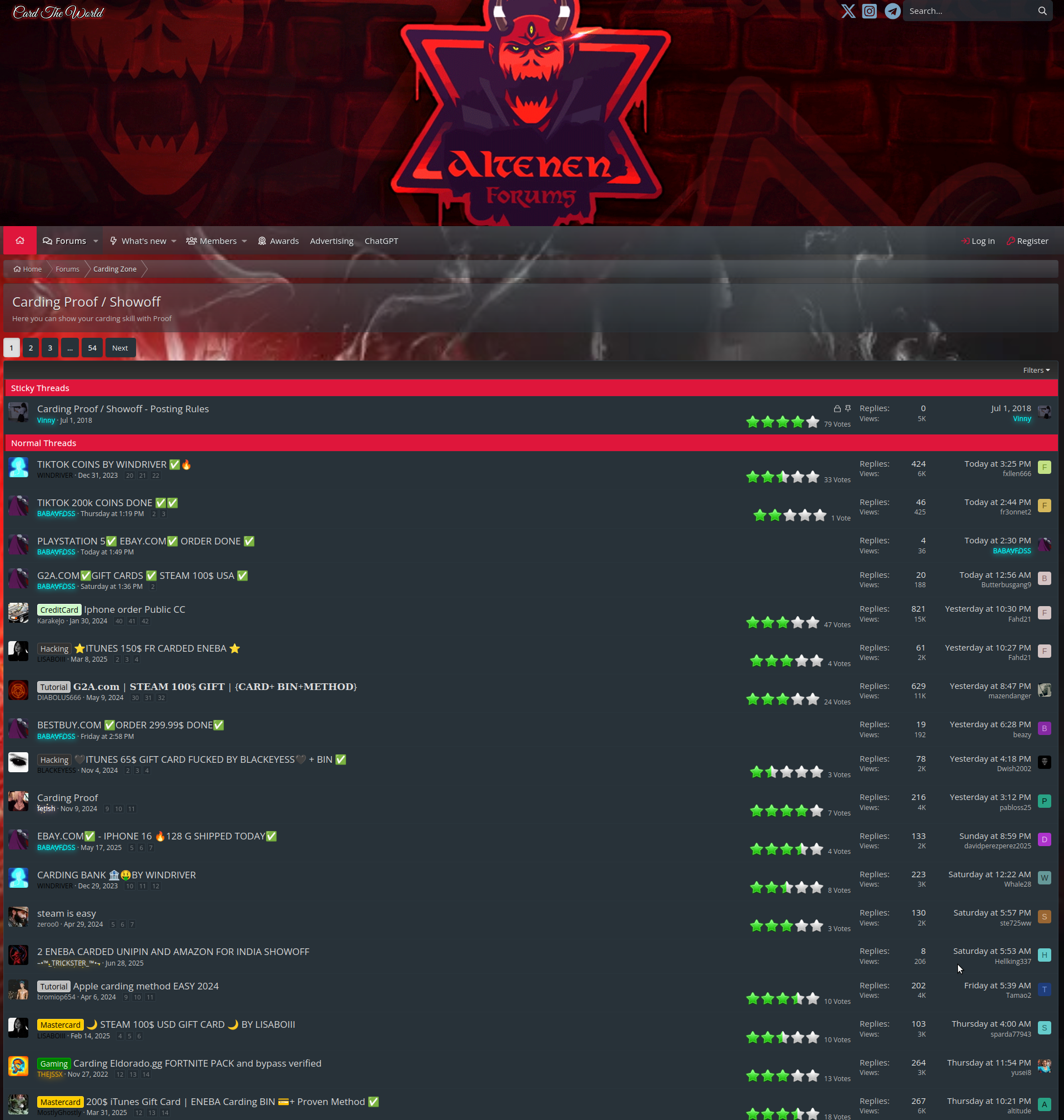
As an analyst, you must understand that not all of these individuals are hardened criminals; some are simply scammers.
These forums operate in plain sight. However, there are other forums that are not as easily accessible. For example, xss.is is a well-known Russian-speaking forum that requires vetting or invitations.
It is worth noting that many cybercriminal groups operate outside the mainstream forums that CTI analysts typically monitor. For example, many Iranian threat actors operate primarily on Telegram, and these groups often go unnoticed because there are few CTI analysts with the language skills and cultural knowledge needed to monitor Persian-speaking communities effectively. This creates significant blind spots in threat monitoring.
Dread
Dread is similar to Reddit. It is one of the main social forums on the dark web and is accessible through the Tor browser. You can find Dread and other dark web sites through resources like dark.fail.
Both criminals and analysts use Dread as a starting point to understand what is happening across different underground sites. It serves as a gateway to other criminal platforms.
Here is a screenshot of a message posted by an administrator of Archetyp:
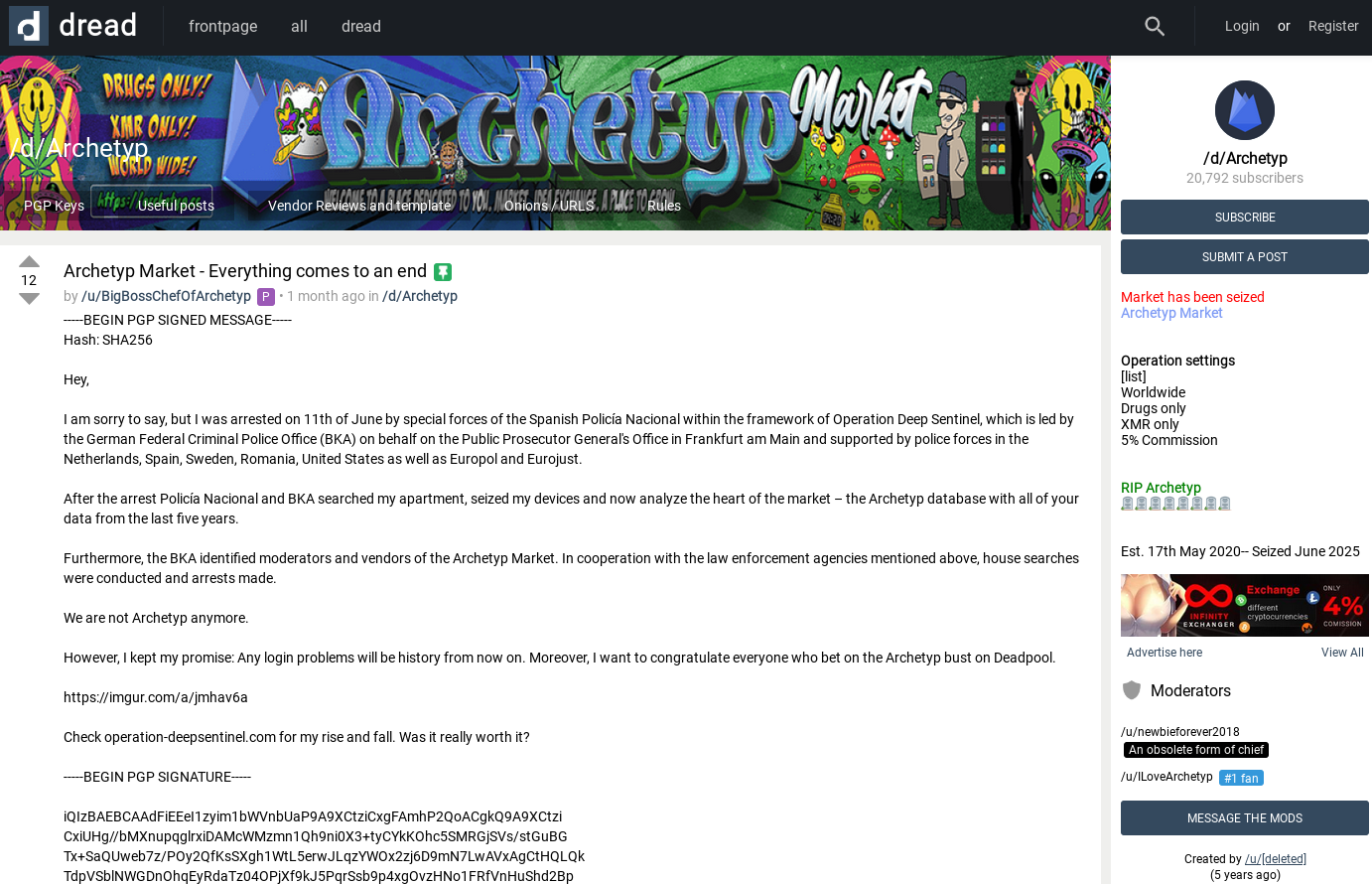
Archetyp was a drug marketplace that was taken down during Operation Deep Sentinel.
While there has long been a sense of mystery around dark web platforms, the reality is often more straightforward than people expect. These sites are simply tools used by criminals to conduct illegal business. That's it.